Front-Running & MEV Mitigation: A DEX Developer's Guide
TL;DR: Front-Running & MEV in DeFi
- MEV (Maximal Extractable Value) is the "invisible tax" on DeFi users, bots and validators profit by reordering, inserting, or censoring transactions in the mempool.
- Front-running, sandwich, and displacement attacks are the most damaging for DEX users.
- Mitigation is multi-layered: Use slippage/deadline checks, commit-reveal schemes, batch auctions, private orderflow (Flashbots Protect), and intent-based systems (CoW Protocol).
- For devs: Enforce slippage/deadline, consider commit-reveal for sensitive actions, explore intent-based architectures, and educate users on private RPCs.
- For users: Use wallets with private RPCs that offer MEV-Share (e.g., Flashbots Protect) to avoid the public mempool and even earn rebates.
1. What is MEV? Why Does It Matter for DEXs?
Maximal Extractable Value (MEV) is the extra value that can be captured by reordering, inserting, or censoring transactions in a block. In DEXs, this means bots and validators can profit at the expense of regular users (especially when trading large amounts or creating new pools).
MEV Supply Chain: The MEV ecosystem involves several actors:
- Searchers: Bots that scan the mempool for profitable opportunities and create transaction bundles.
- Builders: Aggregate bundles and user transactions to construct the most profitable block.
- Validators (Proposers): Choose which block to propose, often selecting the most profitable one.
This supply chain means MEV is not a bug, but a structural feature of transparent, permissionless blockchains (making mitigation a core design challenge for DEXs).
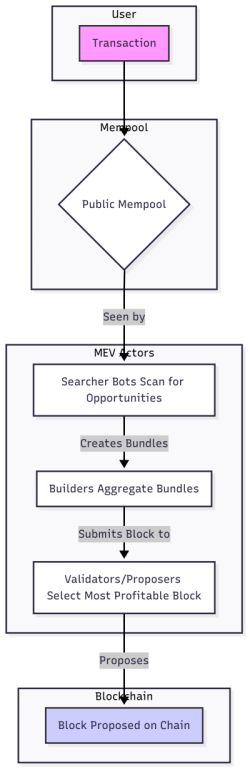 Figure: The MEV supply chain and extraction process in DeFi.
Figure: The MEV supply chain and extraction process in DeFi.
Key MEV Attack Vectors:
- Front-running: An attacker sees your pending trade and jumps ahead, profiting from the price move you create.
- Sandwich attacks: Your trade is sandwiched between a bot's buy and sell, extracting the maximum slippage you allow.
- Displacement attacks: An attacker preempts a unique action (like creating a new pool) with malicious parameters, causing you to lose value or fail.
DEX Example: Suppose you want to create a new liquidity pool with a fair initial price. An attacker sees your transaction in the mempool and quickly creates the pool first, but with malicious parameters (e.g., a skewed price). When your transaction executes, it interacts with the attacker's pool, causing you to lose value or receive fewer LP tokens.
| Attack Type | Victim | Consequence |
|---|---|---|
| Front-running | Trader | Bot profits from your price impact |
| Sandwich | Trader | You get the worst price within your slippage |
| Displacement | LP/Creator | Your action is preempted or manipulated |
2. How Do Front-Running & Sandwich Attacks Work?
Front-Running (Insertion Attack)
- Bot monitors the mempool for profitable trades (e.g., a large buy).
- Bot submits the same trade with a higher gas fee, getting mined first.
- Bot profits from the price change your trade causes.
Sandwich Attack
- Bot sees your swap with a slippage tolerance (e.g., 1%).
- Bot buys before you, pushing the price up.
- Your trade executes at a worse price (max slippage).
- Bot sells after you, locking in profit (your loss is their gain).
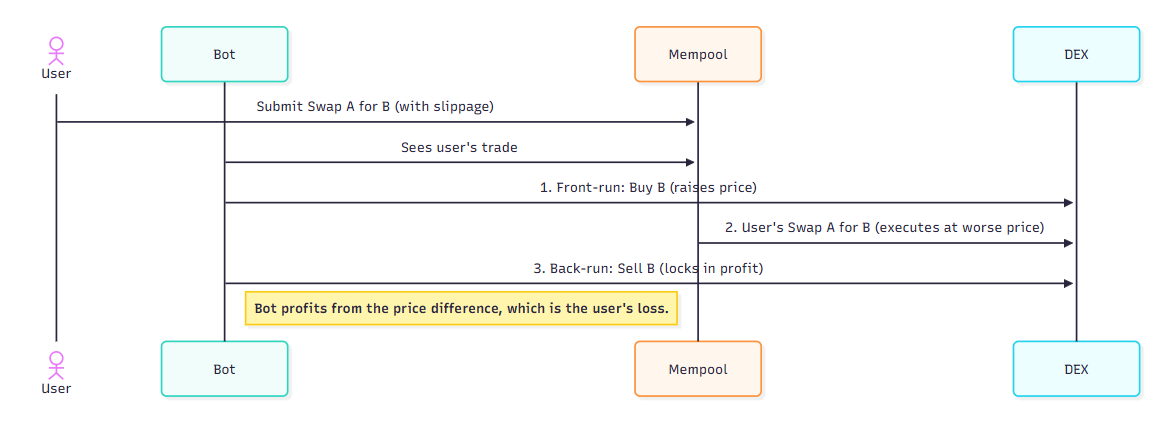 Figure: A sandwich attack sequence: bot buys before and sells after your trade, extracting value from your slippage.
Figure: A sandwich attack sequence: bot buys before and sells after your trade, extracting value from your slippage.
Displacement Attack
- Bot preempts a unique action (e.g., pool creation, NFT mint) with malicious parameters, causing your transaction to fail or be less valuable.
3. Core MEV Mitigation Strategies for DEX Builders
A. Slippage & Deadline Checks (Non-Negotiable!)
- Slippage: Always require
amountOutMin(oramountInMax) in swaps. Revert if the user gets a worse price. - Deadline: Require a
deadlineparameter. Revert if the transaction is mined after this time. - Why: These checks are your first line of defense (don't let users get sandwiched or stuck with stale trades).
Solidity Example:
require(amounts[amounts.length - 1] >= amountOutMin, "Insufficient output amount");
require(block.timestamp <= deadline, "Transaction expired");
B. Commit-Reveal Schemes (Hide User Intent)
- How it works: Users first submit a hash of their trade (commit), then later reveal the details (reveal). Bots can't front-run what they can't see.
- Tradeoff: Adds friction (2 transactions), but powerful for high-value or sensitive actions. Commit-reveal is best for actions where privacy is critical, but it can reduce UX for frequent trades.
Solidity Example:
// Commit phase
function commitSwap(bytes32 commitment) external { ... }
// Reveal phase
function revealAndExecuteSwap(params, salt) external { ... }
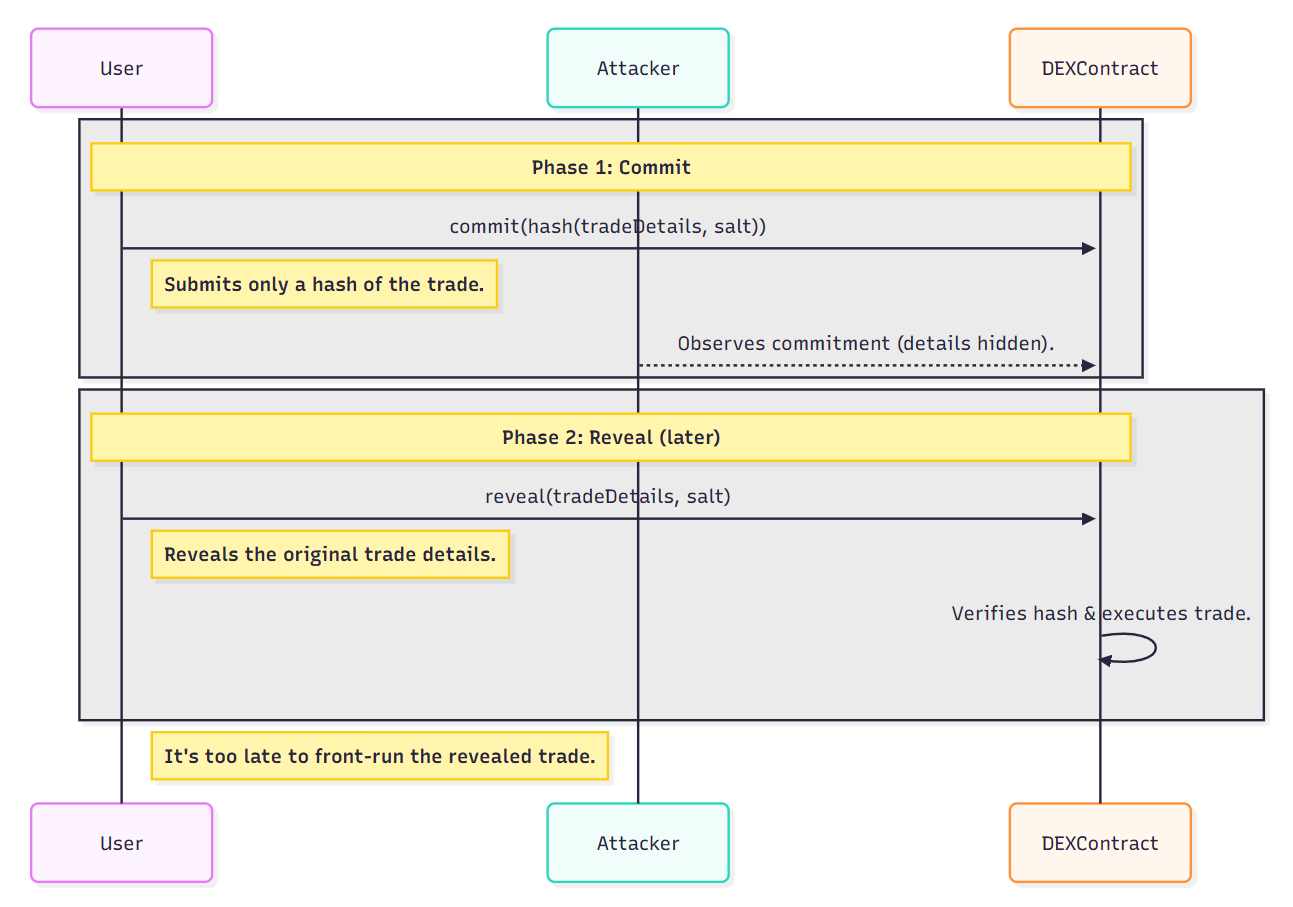 Figure: Commit-reveal scheme: users first commit a hash, then reveal trade details to prevent front-running.
Figure: Commit-reveal scheme: users first commit a hash, then reveal trade details to prevent front-running.
C. Batch Auctions (Neutralize Ordering Attacks)
- How it works: Collect trades over a period, then settle all at a uniform price. No advantage to being first (front-running and sandwiching are neutralized).
- Tradeoff: Complex to implement; often requires off-chain solvers (see CoW Protocol). Batch auctions offer strong protection but fundamentally change the trading model and may not suit all DEXs.
D. Private Orderflow & MEV-Rebates (Flashbots, MEV Blocker)
- How it works: Instead of broadcasting a transaction to the public mempool, users send it to a private relay. Beyond simply hiding transactions, modern relays can enable MEV-Share. This allows your transaction to be safely back-run by searchers who bid for the opportunity, and a portion of the MEV they generate is shared back with you as a rebate. You are protected from front-running and can even earn back some of your trading costs.
- User Guide:
- Add a Private RPC to MetaMask, examples: Flashbots Protect, mevblocker.io, or dRPC (MEV protection only on paid plans):
- Network Name: Flashbots Protect
- RPC URL:
https://rpc.flashbots.net/fast - Chain ID: 1
- Currency Symbol: ETH
- Block Explorer:
https://etherscan.io
- Select this network before trading for MEV protection.
- Add a Private RPC to MetaMask, examples: Flashbots Protect, mevblocker.io, or dRPC (MEV protection only on paid plans):
- Bonus: Failed transactions submitted via private relays don't cost gas! You might even receive an MEV rebate, turning a potential loss into a small gain.
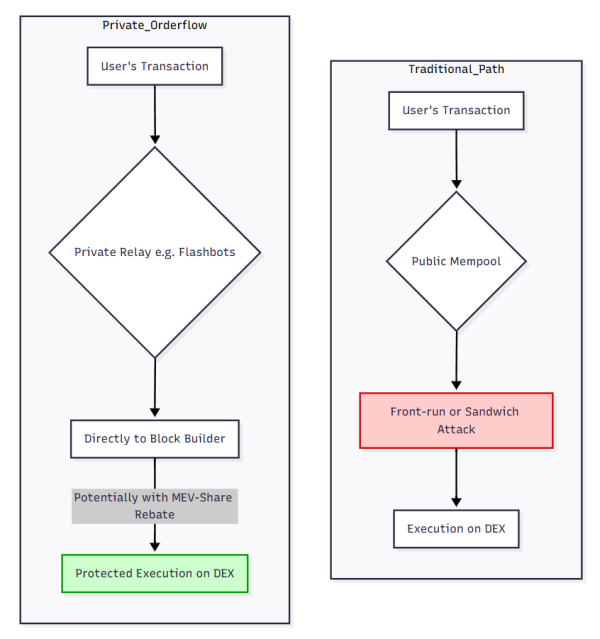 Figure: Private orderflow protects users from front-running and can share MEV rebates back to users.
Figure: Private orderflow protects users from front-running and can share MEV rebates back to users.
E. Fair Sequencing Services (FSS) (Future/Protocol-Level)
- How it works: Decentralized networks (e.g., Chainlink FSS) fairly order transactions before block production. A core technology enabling this is the encrypted mempool, where transactions are submitted in an encrypted state and only decrypted after a final order has been established. This makes front-running impossible without relying on a centralized relay. Projects like Shutter Network are actively developing this tech.
- MEV on Layer 2s: On L2s, MEV presents a different challenge. Many L2s rely on a centralized sequencer, which can reorder or censor transactions without public competition. The long-term solution involves decentralizing sequencers or using models like based sequencing, where the underlying L1 helps guarantee a fair ordering, making FSS a critical component for the L2 future.
- Status: Still experimental, but promising for L2s and the future of Ethereum.
F. Adopting Intent-Based Architectures
- How it works: This is a shift from imperative transactions (e.g., "swap X for Y on this DEX") to declarative intents (e.g., "I want to end up with at least Y tokens, and I'm willing to spend at most X tokens"). Users sign these intents, and a network of off-chain "solvers" competes to find the best possible way to execute them across any number of venues (DEXs, private liquidity, etc.).
- Why it stops MEV: The execution path is never broadcast to the public mempool, so there is nothing to front-run or sandwich. Solvers are responsible for execution and finding the best price. DEXs like CoW Protocol are pioneers in this space, combining intents with batch auctions for powerful MEV protection.
- The Future:
transaction -> public mempool -> MEV riskbecomesintent -> solver network -> optimized execution -> MEV protection.
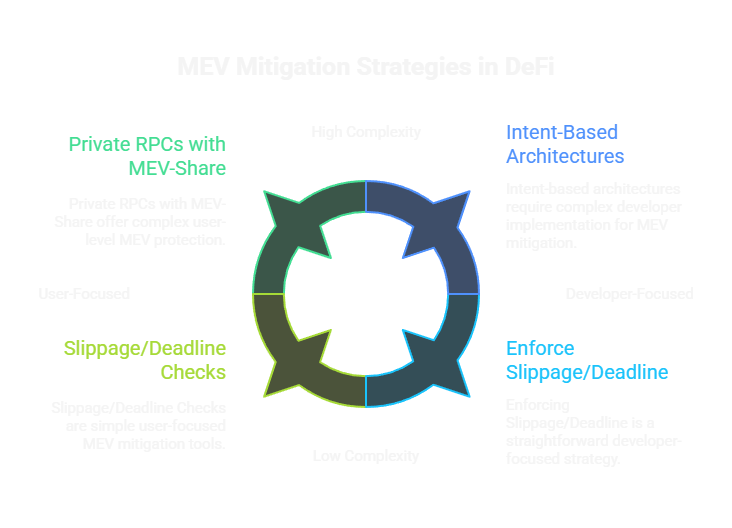 Figure: Overview of core MEV mitigation strategies for DEX builders and users.
Figure: Overview of core MEV mitigation strategies for DEX builders and users.
4. Developer Checklist: MEV-Resistant DEX
- [ ] Slippage controls (
amountOutMin/amountInMax) enforced in every swap? - [ ] Deadline parameter enforced in every state-changing function?
- [ ] Displacement protection for unique actions (e.g., pool creation)?
- [ ] Commit-reveal for high-value or sensitive user actions?
- [ ] Reentrancy protection (use
nonReentrantfor multi-token/external calls)? - [ ] User docs/UI encourage private RPCs (Flashbots Protect)?
- [ ] No on-chain randomness (block.timestamp, block.number) for critical logic?
- [ ] Security audit before mainnet deployment?
5. User Tips: How to Avoid Getting Sandwiched
- Use wallets with private RPCs (e.g., Flashbots Protect, mevblocker.io) for all DEX trades.
- Set tight slippage tolerances, never use high slippage unless you understand the risk.
- Check deadlines, don't let transactions sit in the mempool.
- Avoid trading illiquid pairs since they're easier targets for MEV bots.
- Stay informed, follow DEX and wallet updates for new MEV protection features.
6. Summary: Building & Using MEV-Resistant DEXs
MEV is a fact of life in DeFi, but you can fight back. As a builder, enforce slippage/deadline, consider commit-reveal or batch auctions, and educate your users. As a user, use private RPCs and set tight slippage. Together, we can make the Dark Forest a little less dangerous.
Mitigation Strategy Trade-offs:
- Slippage/Deadline: Easy to implement, limits damage but doesn't prevent MEV.
- Commit-Reveal: Strong for privacy, but adds friction (2 transactions).
- Batch Auctions: Excellent protection, but complex and changes trading UX.
- Private Orderflow: Great for users, easy to adopt, but relies on external infrastructure.
- FSS: Theoretical, protocol-level fix.
Ready to build a secure DEX? Try the Minimum Viable Exchange (Dex) Challenge!