Flash Loan Exploits: A Developer's Guide to Securing Your DEX
TL;DR: Flash Loan Exploits & DEX Security
- Flash loans are uncollateralized loans that must be repaid within a single transaction. They're not inherently malicious but can weaponize existing vulnerabilities.
- Common attack vectors: Price oracle manipulation, reentrancy attacks, governance takeovers, and complex logic flaws.
- Defensive patterns: Use Time-Weighted Average Price (TWAP) oracles instead of spot prices, implement Checks-Effects-Interactions (CEI) pattern, and add ReentrancyGuard.
- Real-world impact: Over $1 billion lost to flash loan attacks, with PancakeBunny ($45M), Cream Finance ($18.8M), Beanstalk ($182M), and Euler Finance ($197M) among the largest.
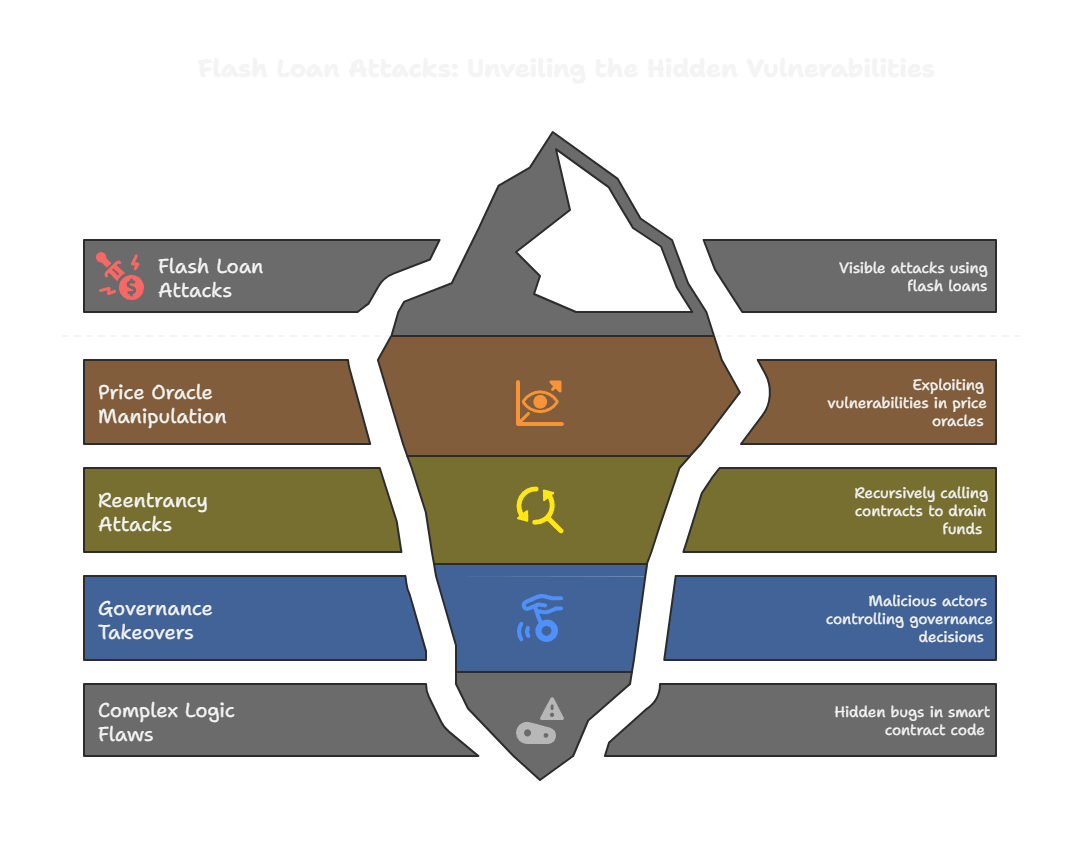 Figure: Overview of how flash loan attacks exploit vulnerabilities in DeFi protocols.
Figure: Overview of how flash loan attacks exploit vulnerabilities in DeFi protocols.
1. Understanding Flash Loans: The Double-Edged Sword of DeFi
Flash loans are one of DeFi's most powerful innovations and its most dangerous weapons. A flash loan is an uncollateralized loan that must be borrowed and repaid within a single, atomic blockchain transaction. If the loan isn't repaid by the transaction's end, the entire operation reverts as if it never happened.
This mechanism enables legitimate use cases like arbitrage, collateral swaps, and liquidations. However, it also gives attackers temporary access to massive capital, turning them into "whales for a block" who can exploit existing vulnerabilities in your smart contracts.
Key Insight: Flash loans don't create vulnerabilities, they expose them. Any user can wield infinite capital for one transaction, fundamentally changing your security threat model.
The Threat Model Shift: Flash loans democratize attack capability. Previously, exploiting economic vulnerabilities required millions in capital, a significant barrier. Now, any user can access near-infinite capital for one transaction, requiring developers to design contracts assuming maximum adversarial resources.
For developers building DEXs and DeFi protocols, understanding flash loan attack vectors is essential. This guide will show you how to build resilient systems that can withstand these sophisticated attacks.
Every flash loan attack follows a universal pattern:
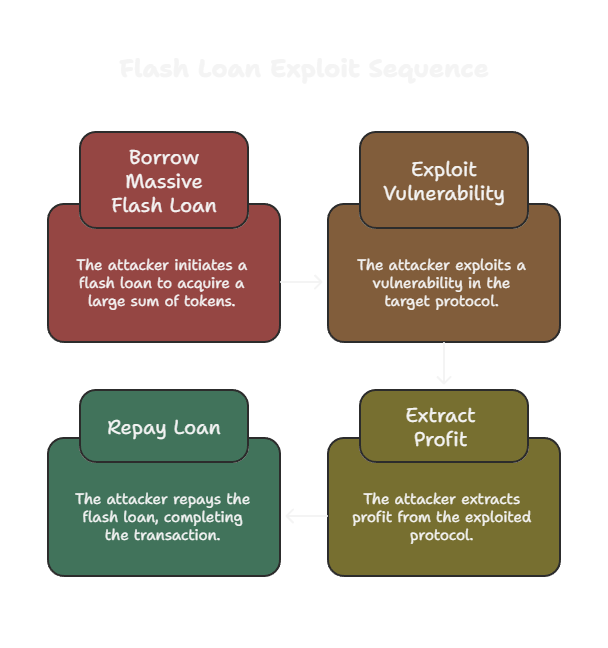 Figure: The typical sequence of a flash loan exploit: borrow, manipulate, profit, and repay.
Figure: The typical sequence of a flash loan exploit: borrow, manipulate, profit, and repay.
Step 1: Borrow
The attacker takes a massive flash loan (often hundreds of millions of dollars) from protocols like Aave, dYdX, or Uniswap.
Step 2: Manipulate
The borrowed capital exploits a pre-existing vulnerability in your protocol, typically price oracle manipulation, reentrancy, governance logic flaws, or complex business logic errors.
Step 3: Profit & Repay
After extracting value, the attacker repays the flash loan plus fees and pockets the difference.
Example Attack Flow:
// 1. Borrow massive flash loan
flashLoan(1000000 * 10**18); // 1M tokens
// 2. Exploit vulnerability
exploitTargetProtocol();
// 3. Extract profit
extractValue();
// 4. Repay loan (or transaction reverts)
repayFlashLoan();
3. Case Study 1: Price Oracle Manipulation — PancakeBunny ($45M)
The PancakeBunny exploit demonstrates the dangers of trusting simple on-chain spot prices.
The Vulnerability
PancakeBunny calculated BUNNY token values using direct spot prices from PancakeSwap liquidity pools. This assumed the pool's asset ratio always reflected fair market value, a fatal assumption.
The Root Problem: AMM spot prices reflect only the last trade in that isolated pool (governed by the x×y=k invariant), not global market value. With sufficient capital (provided by flash loans), these prices are easily manipulated.
The Exploit
- Borrow: 2.3M BNB (worth $700M+) via flash loan
- Manipulate: Massive swap of BNB for USDT, skewing the pool's price ratio
- Exploit: Protocol read the manipulated price and minted illegitimate BUNNY tokens
- Profit: Sold 7M BUNNY tokens for 2.3M WBNB + 2.9M USDT
- Repay: Returned the flash loan with $45M profit
The Root Cause
Using a single, synchronous spot price as an oracle. The attacker didn't need to convince the entire market that BNB's price had changed, they only needed to convince the single, vulnerable smart contract listening to the wrong signal.
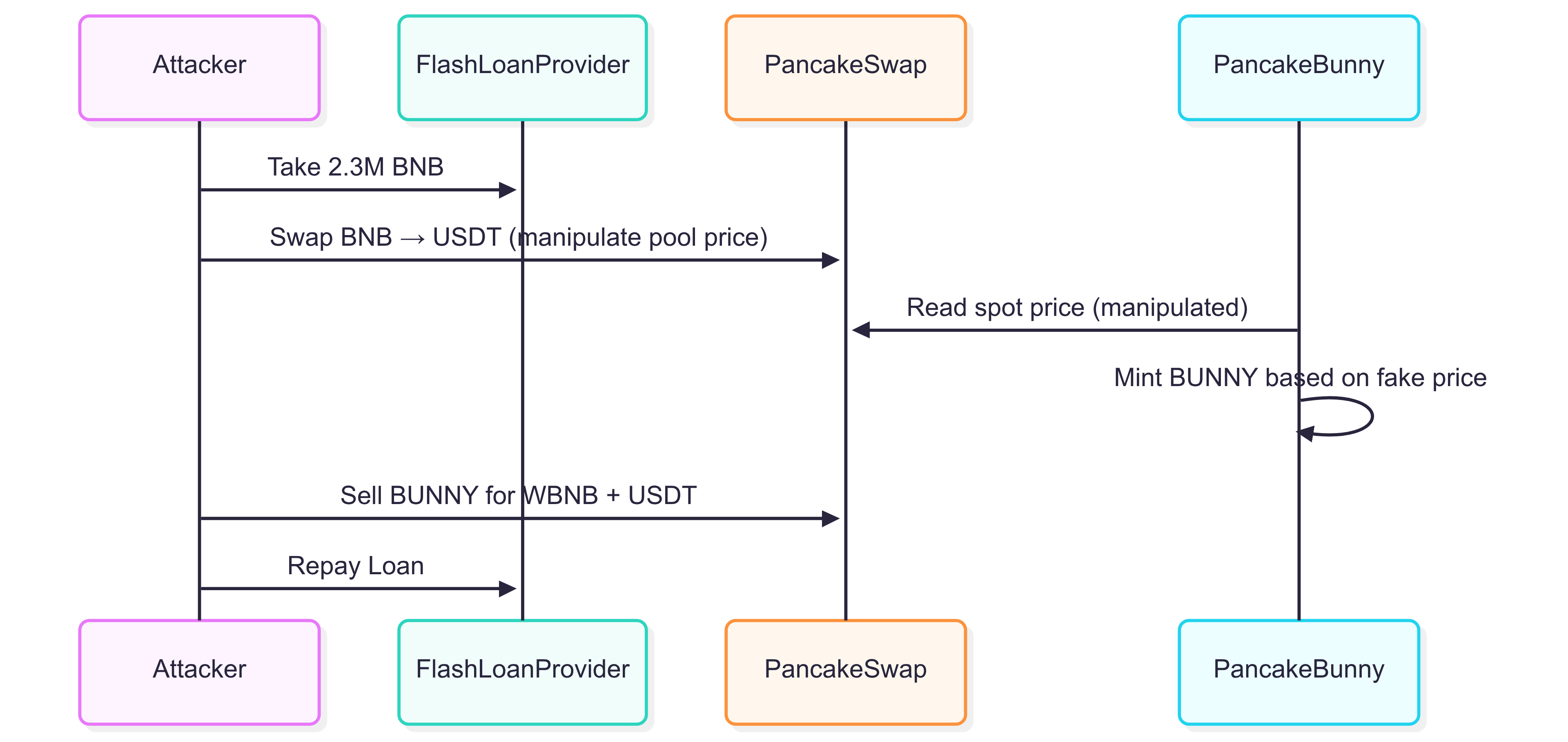 Figure: How the PancakeBunny attacker manipulated prices and extracted profit using a flash loan.
Figure: How the PancakeBunny attacker manipulated prices and extracted profit using a flash loan.
4. Defensive Pattern 1: Time-Weighted Average Price (TWAP) Oracles
The solution to price oracle manipulation is incorporating time into your price calculations.
Why TWAP Works
TWAP oracles calculate average prices over time, making them resistant to single-transaction manipulation. An attacker would need to sustain artificial prices across multiple blocks, prohibitively expensive and defeating the purpose of a cheap flash loan.
The Technical Foundation: Uniswap V2 stores cumulative price variables (price0CumulativeLast and price1CumulativeLast) that represent a running sum of spot prices multiplied by time elapsed. By reading these values at two points and calculating the difference, you get a time-weighted average.
Uniswap V3 Improvements: Uniswap V3 significantly improved on-chain oracles by maintaining an array of observations (time-stamped cumulative tick values). This makes it more gas-efficient and less complex to get a robust TWAP, as you can query the chain directly for a time-weighted average over a specific period without needing to call an update function yourself.
TWAP Limitations: TWAPs are not a panacea. They can lag during periods of legitimate high volatility. A very long TWAP window makes the oracle unresponsive, while a very short one can still be vulnerable to manipulation across multiple blocks (though at a much higher cost).
Uniswap V2 TWAP Implementation
Uniswap V2 stores cumulative price variables that enable efficient TWAP calculations:
// SPDX-License-Identifier: MIT
pragma solidity ^0.8.18;
import "@uniswap/v2-core/contracts/interfaces/IUniswapV2Pair.sol";
contract TWAPOracle {
struct Observation {
uint32 blockTimestamp;
uint256 price0Cumulative;
uint256 price1Cumulative;
}
mapping(address => Observation) public pairObservations;
function update(address pairAddress) external {
(uint256 price0Cumulative, uint256 price1Cumulative, uint32 blockTimestamp) =
IUniswapV2Pair(pairAddress).price0CumulativeLast();
pairObservations[pairAddress] = Observation({
blockTimestamp: blockTimestamp,
price0Cumulative: price0Cumulative,
price1Cumulative: price1Cumulative
});
}
function consult(address pairAddress, uint256 amountIn, address tokenIn)
external view returns (uint256 amountOut) {
Observation memory lastObservation = pairObservations[pairAddress];
require(lastObservation.blockTimestamp > 0, "Oracle not initialized");
(uint256 price0Cumulative, uint256 price1Cumulative, uint32 blockTimestamp) =
IUniswapV2Pair(pairAddress).price0CumulativeLast();
uint32 timeElapsed = blockTimestamp - lastObservation.blockTimestamp;
require(timeElapsed > 0, "Oracle update required");
// Calculate average price over the period
// Note: Uniswap uses UQ112.112 fixed-point numbers for prices
uint256 price0Average = (price0Cumulative - lastObservation.price0Cumulative) / timeElapsed;
uint256 price1Average = (price1Cumulative - lastObservation.price1Cumulative) / timeElapsed;
address token0 = IUniswapV2Pair(pairAddress).token0();
if (tokenIn == token0) {
amountOut = (amountIn * price0Average) / price1Average;
} else {
amountOut = (amountIn * price1Average) / price0Average;
}
}
}
Key Insight: By subtracting an old cumulative value from the current one and dividing by time elapsed, you derive an average price that's insulated from short-term manipulations.
Production Recommendation
For mission-critical applications, use decentralized oracle networks like Chainlink instead of building your own. Chainlink Price Feeds are secure because they aggregate prices from numerous independent, high-quality data aggregators off-chain and have decentralized oracle networks to report them on-chain, making them resistant to single-source manipulation (like an on-chain DEX pool) and resilient to temporary on-chain network congestion or block-level manipulation.
Build vs. Buy Decision: While building a simple TWAP oracle is excellent for learning, production systems benefit from multi-source aggregation that single-DEX oracles can't provide.
5. Case Study 2: Reentrancy — Cream Finance ($18.8M)
The Cream Finance hack shows how classic vulnerabilities can reappear through protocol composition, particularly with non-standard token implementations.
The Vulnerability
Cream Finance integrated AMP tokens (ERC-777) into their lending market. ERC-777 includes _callPostTransfersHook, which allows recipient contracts to execute code during transfers, unlike ERC-20's simple transfer mechanism.
The critical flaw: Cream's borrow() function transferred AMP tokens before updating the user's debt balance, violating the Checks-Effects-Interactions pattern.
The Exploit
- Attacker calls
borrow()with sufficient collateral - Cream transfers AMP tokens to attacker's contract
- Reentrancy: AMP's
tokensReceivedhook triggers, giving control to attacker - Attacker immediately calls
borrow()again - Cream's state still shows full collateral available (not yet updated)
- Loop: This creates a recursive drain of AMP tokens
The Root Cause
Violating the Checks-Effects-Interactions pattern by performing external calls before updating internal state. The ERC-777 hook mechanism provided the reentrancy vector that wouldn't exist with standard ERC-20 tokens.
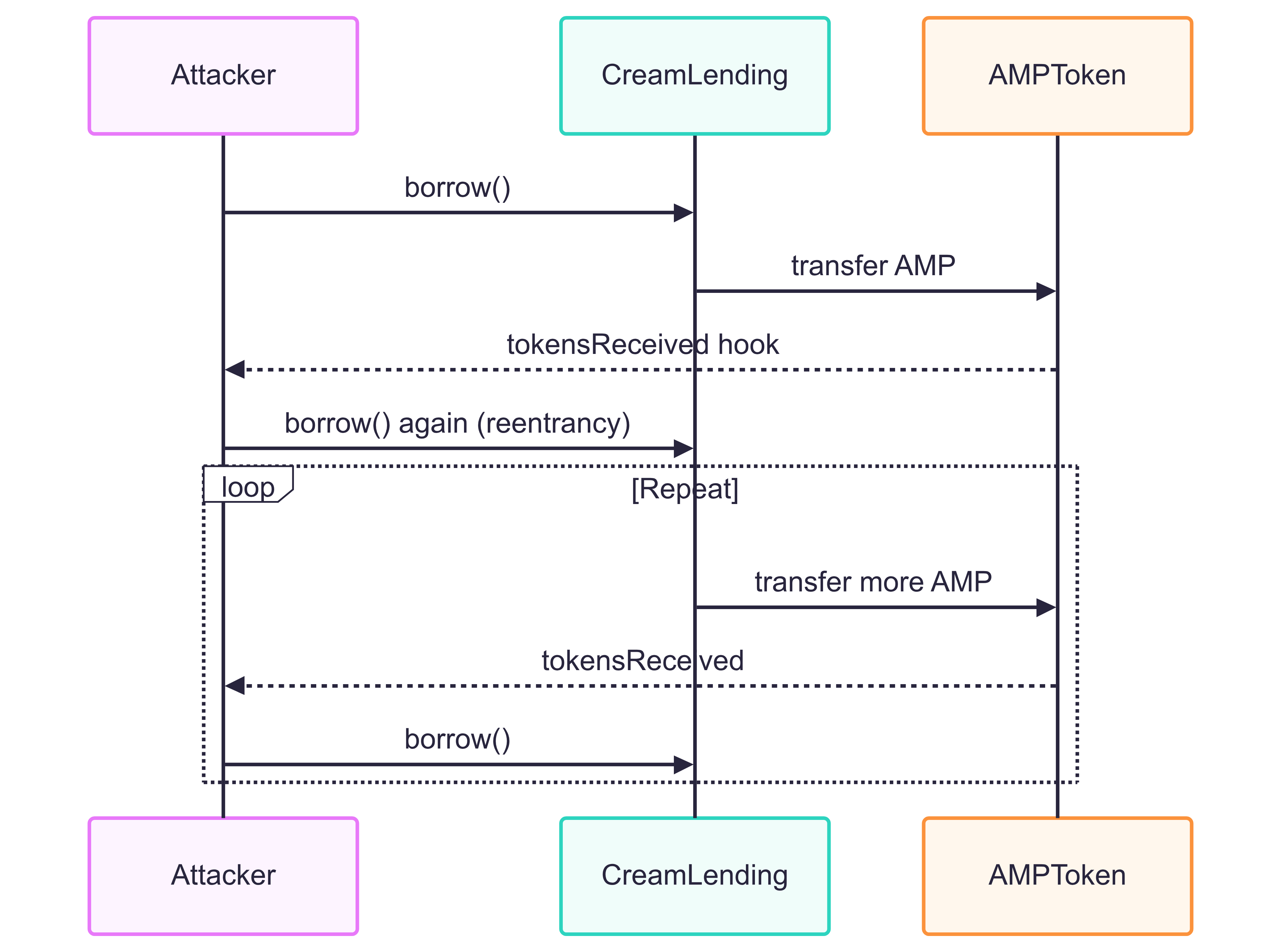 Figure: The Cream Finance reentrancy exploit flow, enabled by improper state updates and ERC-777 hooks.
Figure: The Cream Finance reentrancy exploit flow, enabled by improper state updates and ERC-777 hooks.
6. Defensive Pattern 2: Preventing Reentrancy with CEI & Guards
Reentrancy is a solved problem in modern Solidity development.
The Checks-Effects-Interactions (CEI) Pattern
Structure your functions in this specific order:
- Checks: Validate all inputs and conditions
- Effects: Update your contract's state variables
- Interactions: Make external calls to other contracts
Vulnerable vs. Secure Code:
// VULNERABLE: Interaction before Effect
function withdraw() public {
uint256 amount = balances[msg.sender];
require(amount > 0, "No balance");
// DANGEROUS: External call before state update
(bool success, ) = msg.sender.call{value: amount}("");
require(success, "Transfer failed");
// TOO LATE: Balance updated after call
balances[msg.sender] = 0;
}
// SECURE: Checks-Effects-Interactions
function withdraw() public {
// 1. CHECK
uint256 amount = balances[msg.sender];
require(amount > 0, "No balance");
// 2. EFFECT (update state first)
balances[msg.sender] = 0;
// 3. INTERACTION (now safe)
(bool success, ) = msg.sender.call{value: amount}("");
require(success, "Transfer failed");
}
OpenZeppelin's ReentrancyGuard
For maximum security, use OpenZeppelin's battle-tested ReentrancyGuard:
import "@openzeppelin/contracts/security/ReentrancyGuard.sol";
contract SecureBank is ReentrancyGuard {
mapping(address => uint256) public balances;
function withdraw(uint256 amount) external nonReentrant {
require(balances[msg.sender] >= amount, "Insufficient");
balances[msg.sender] -= amount;
(bool sent, ) = msg.sender.call{value: amount}("");
require(sent, "Withdraw failed");
}
}
The nonReentrant modifier prevents any reentrant calls to the function, providing an explicit security layer.
7. Case Study 3: Complex Logic Flaws — Euler Finance ($197M)
The Euler Finance hack demonstrates how flash loans can be just the entry point for exploiting intricate protocol-specific business logic flaws.
The Exploit
In March 2023, an attacker executed a highly complex exploit:
- Flash Loan Entry: Borrowed DAI via flash loan
- Self-Collateralizing Position: Deposited DAI as collateral, then used a "leveraged" borrow against the same collateral
- Logic Exploitation: Exploited a flaw in the donation logic to create bad debt in the protocol
- Profit Extraction: Made their position appear healthier than it was, allowing liquidation at massive profit
- Flash Loan Exit: Repaid the loan with $197M profit
The Root Cause
This wasn't a simple oracle or reentrancy issue, it was a complex flaw in Euler's internal accounting and liquidation logic. The flash loan was merely the tool that provided the capital needed to exploit the underlying business logic vulnerability.
Key Lesson: Flash loans are often just the entry point for exploiting intricate protocol-specific business logic flaws that require significant capital to trigger.
8. Case Study 4: Governance Takeovers — Beanstalk ($182M)
Flash loans can attack not just code, but governance structures and protocol processes.
The Exploit
In April 2022, an attacker:
- Borrowed: $1 billion in stablecoins via flash loan
- Purchased: Massive quantity of Stalk (Beanstalk's governance token)
- Voted: Used temporary 67% voting power to pass malicious proposal BIP-18
- Drained: Transferred all $182M in protocol collateral to attacker's address
- Repaid: Flash loan and vanished with profit
The Vulnerability
Beanstalk's governance allowed immediate execution of proposals with super-majority votes. The attacker weaponized this "emergency" feature intended for rapid defense against the protocol itself.
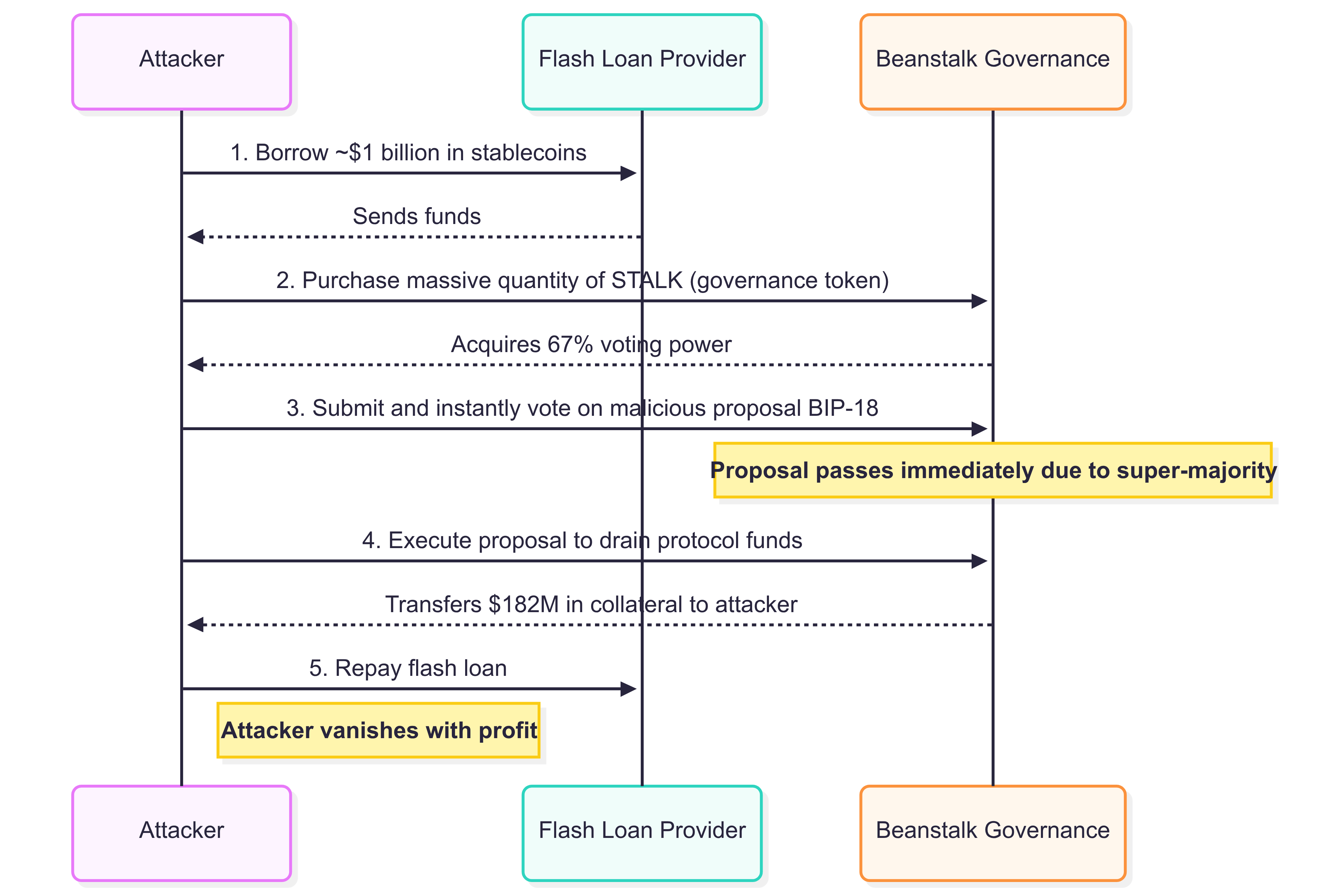 Figure: Beanstalk governance exploit: attacker uses a flash loan to gain voting power and drain protocol funds.
Figure: Beanstalk governance exploit: attacker uses a flash loan to gain voting power and drain protocol funds.
Higher-Order Effect: This case reveals how flash loans can exploit vulnerabilities not just in code, but in process and design. The governance was designed for agility but failed to consider a threat model where an attacker could acquire temporary super-majority.
The Defense: Enhanced Governance Security
Implement mandatory delays between proposal passage and execution:
contract TimelockController {
uint256 public constant MIN_DELAY = 24 hours;
uint256 public constant MIN_QUORUM = 10; // 10% of total supply
mapping(bytes32 => uint256) public _timestamps;
mapping(bytes32 => uint256) public _voteCounts;
function schedule(bytes32 id, uint256 delay) external {
require(delay >= MIN_DELAY, "Delay too short");
_timestamps[id] = block.timestamp + delay;
}
function execute(bytes32 id) external {
require(_timestamps[id] <= block.timestamp, "Too early");
require(_voteCounts[id] >= MIN_QUORUM, "Insufficient quorum");
// Execute the proposal
}
}
Beyond Timelocks: Additional governance safeguards include requiring a minimum vote quorum (a minimum percentage of total tokens that must participate) and a voting threshold (the percentage of votes needed to pass a proposal). Beanstalk's flaw was partly that an attacker could both acquire the tokens and vote to execute in one transaction. A quorum and a delay would have required broader, more sustained participation.
This delay acts as a circuit breaker, giving the community time to react to malicious proposals. The attacker's voting power would vanish after repaying the flash loan, long before the delay elapsed.
9. Building a Secure DEX: Best Practices Summary
Price Oracle Security
- ❌ Never use single spot prices from DEX pools
- ✅ Use TWAP oracles for on-chain calculations
- ✅ Consider Uniswap V3 for more efficient oracle queries
- ✅ Integrate Chainlink for production systems
- ✅ Implement price deviation checks to detect manipulation
- ✅ Consider multi-source aggregation for critical applications
Reentrancy Protection
- ✅ Always follow Checks-Effects-Interactions pattern
- ✅ Use ReentrancyGuard for functions with external calls
- ✅ Test thoroughly with reentrancy attack scenarios
- ✅ Audit your code before mainnet deployment
- ✅ Be cautious with non-standard tokens (ERC-777, etc.)
Governance Security
- ✅ Implement time-locks on all critical functions
- ✅ Use multi-sig wallets for administrative actions
- ✅ Consider governance delays proportional to proposal impact
- ✅ Monitor for unusual voting patterns
- ✅ Design for temporary super-majority attacks
- ✅ Require minimum quorum for governance decisions
General Security
- ✅ Treat all external contracts as untrusted
- ✅ Check return values from all external calls
- ✅ Use audited libraries like OpenZeppelin
- ✅ Implement circuit breakers for emergency pauses
- ✅ Design defensively assuming maximum adversarial resources
- ✅ Audit business logic for complex financial operations
10. Testing Your Defenses
Flash Loan Attack Simulation
Test your contracts against realistic attack scenarios:
contract FlashLoanAttackTest {
function testPriceOracleManipulation() public {
// 1. Deploy your DEX
// 2. Take flash loan
// 3. Attempt price manipulation
// 4. Verify your defenses hold
}
function testReentrancyAttack() public {
// 1. Create malicious contract with reentrant calls
// 2. Attempt to exploit withdrawal functions
// 3. Verify CEI pattern prevents attack
}
function testComplexLogicFlaws() public {
// 1. Test edge cases in business logic
// 2. Verify accounting remains consistent
// 3. Test liquidation mechanisms
}
}
Key Test Scenarios
- Price manipulation with large capital amounts
- Reentrancy attacks on all external call functions
- Governance takeover attempts
- Edge cases with extreme price movements
- Non-standard token interactions (ERC-777, etc.)
- Complex business logic edge cases
11. Real-World Impact & Lessons Learned
Notable Flash Loan Attacks
| Protocol | Date | Amount | Primary Vulnerability |
|---|---|---|---|
| PancakeBunny | May 2021 | $45M | Price Oracle Manipulation |
| Cream Finance | Aug 2021 | $18.8M | Reentrancy (ERC-777) |
| Beanstalk Farms | Apr 2022 | $182M | Governance Takeover |
| Euler Finance | Mar 2023 | $197M | Logic Flaw & Oracle Manipulation |
Key Lessons
- Flash loans expose weaknesses, they don't create them
- Never trust spot prices for critical calculations
- Reentrancy is preventable with proper patterns
- Governance needs time-locks to prevent takeovers
- Security is a prerequisite, not a feature
- Threat modeling must account for infinite capital scenarios
- Protocol composition can introduce unexpected attack vectors
- Complex business logic requires thorough auditing
12. Conclusion: Building Resilient DeFi
Flash loan attacks have been a painful but necessary catalyst for DeFi security maturation. These exploits underscore that security is fundamental to building trustworthy financial protocols.
The Path Forward
- Design defensively: Assume any user can wield infinite capital
- Use proven patterns: TWAP oracles, CEI, ReentrancyGuard
- Test thoroughly: Simulate realistic attack scenarios
- Audit everything: Get independent security reviews
- Stay current: Follow emerging security best practices
- Consider protocol composition: How integrations affect security
- Audit business logic: Complex financial operations need special attention
By implementing these defensive patterns, you're not just protecting your protocol, you're contributing to a more secure DeFi ecosystem.
Ready to build secure DeFi? Try the Minimum Viable Exchange (Dex) Challenge!
Want to learn more about token security? Check out the ERC20 Approve Pattern Guide!